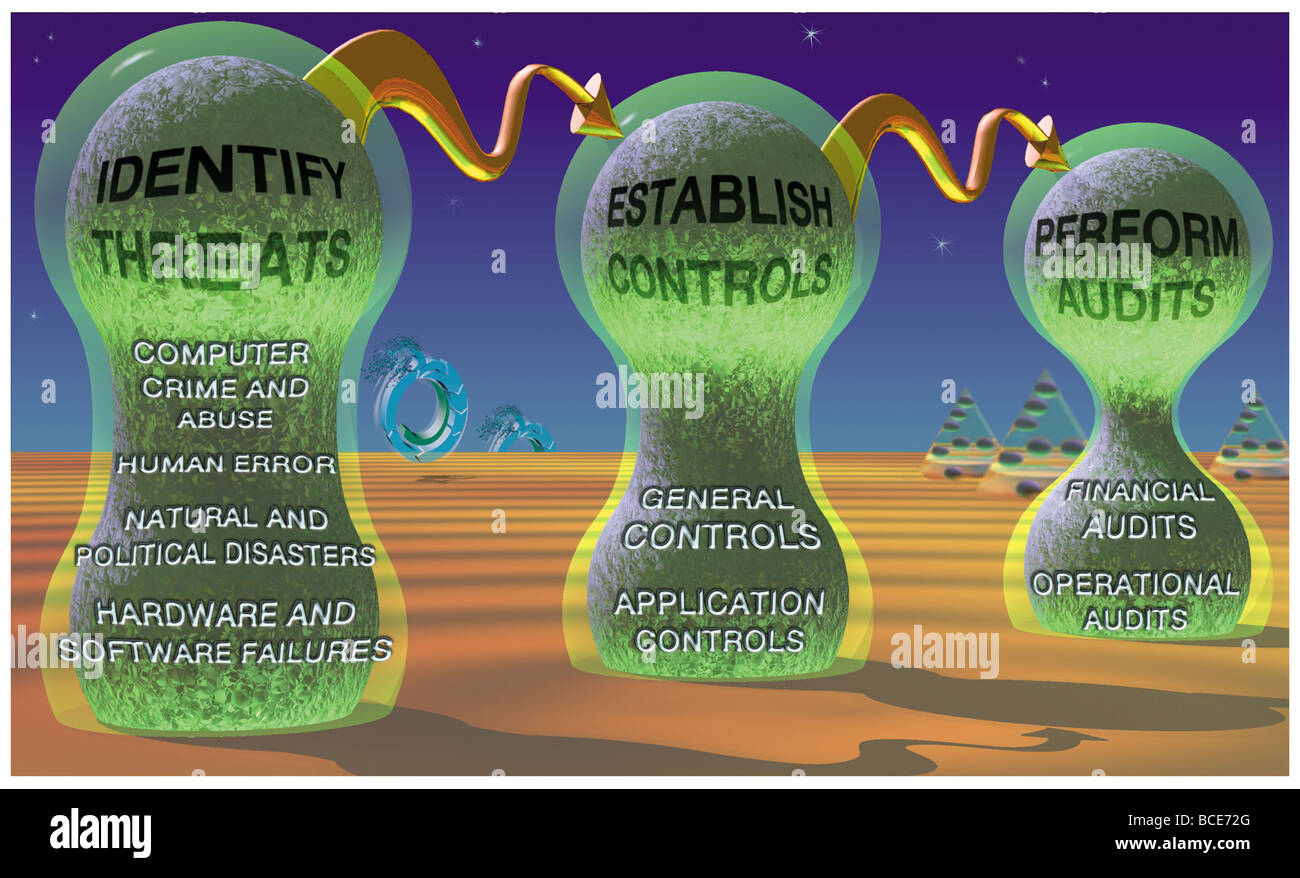
The steps in creating a secure information system: identify threats, establish controls and perform audits to discover breaches.
RMID:Image ID:BCE72G
Image details
Contributor:
Universal Images Group North America LLC / Alamy Stock PhotoImage ID:
BCE72GFile size:
11.2 MB (540.2 KB Compressed download)Releases:
Model - no | Property - noDo I need a release?Dimensions:
2541 x 1542 px | 21.5 x 13.1 cm | 8.5 x 5.1 inches | 300dpiPhotographer:
Encylopaedia BritannicaMore information:
This image could have imperfections as it’s either historical or reportage.
illustrations, illustration, information, systems, knowledge, workplace, structure, management, organizations, professional, employment, employer, executive, resources, conceptual, diagram, figure, cycle, stages, steps, design, programming, testing, installation, operation, maintenance, installing, operating, computing, computer, technology, technological, security, secure, threat, breach, control, audit, horizontal